MeshCentral - Authenticode Time Stamp, Resources, Assistant Lock, Intel® SM, Router
MeshCentral is an open source, web based, feature packed computer management web site. MeshCentral development is continuing swiftly, and the blog posts are not keeping up with the number of features being released, so, this week’s post includes plenty of unrelated features and improvements that are making MeshCentral most customized and more secure than ever before. We have many improvements to the Authenticode feature we announced a few weeks back, code to change the resource strings within an executable, MeshCentral Assistant now has the server locking feature, Intel® Standard Manageability support was improved and more improvements to MeshCentral Router. It’s been a crazy month so far and it’s not over. In detail:
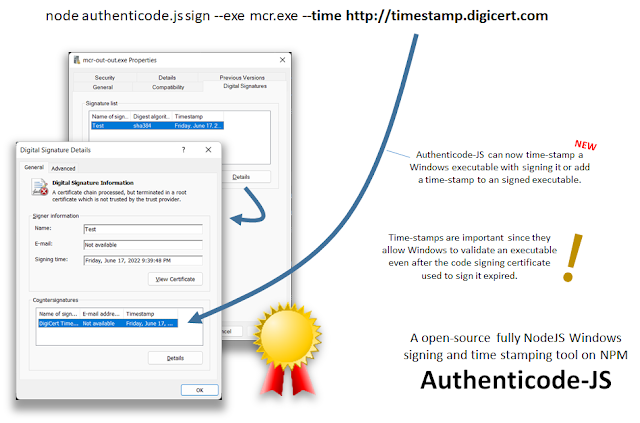
- Authenticode-JS Time Stamping. A few weeks back we released Authenticode-JS, the first ever fully NodeJS tool for code signing Windows executables. This last week, we improved this tool to add support for certificate authority time stamping. This allows an executable that is signed by a trusted code signing certificate to remain valid even after the certificate used to sign the executable expires. With time stamping, the Windows operating system can verify that the executable was signed during the certificate’s validity period. This tool makes it possible to sign and time-stamp Windows executables from any OS including Linux, which is super useful in the server world.
- Authenticode-JS Resource Modifications. In addition to signing and time-stamping a Windows executable, Authenticode-JS can now look at the different sections of a Windows executable and completely break apart the resource section (.rsrc) and allow modifications to be made to the version strings and then reassemble the executable with a re-encoded resource section. This allows a user to edit the version information of an executable prior to signing and time stamping it. This allows an executable to be customized to an organization like never before.
- Time Stamping and Resource Modification in MeshCentral. Authenticode-JS is released as an open-source stand-alone tool for anyone to use, but its primary purpose is its integration into MeshCentral. Starting this week, MeshCentral will automatically time stamp the MeshAgent and a new option is available to disable this feature or change the default time-stamping server used. In addition, you can now set agent version string information to be included in the agent. When set, MeshCentral will place these strings inside the agent resource section before performing code signing and time stamping.
- MeshCentral Assistant Sign-Lock feature. When code signing MeshCentral Assistant, you now have the option to lock the signed binary so that it can only connect to a specific server. The lock includes the DNS name of the server and the server certificate hash. This makes is impossible to use a signed MeshCentral Assistant on any server by your server and so, preserving the trust of your certificate. This feature was included in the MeshAgent at the beginning of the year but is now also in MeshCentral Assistant with the same signing URL format to perform the lock.
- Improved Intel® Standard Manageability (Intel® SM) support. Intel® Standard Manageability includes some of the features of Intel® AMT on lower-cost platforms. Starting this week, MeshCentral has better support for these platforms. MeshCentral will detect this platform type for both agent based and agent-less device groups and will now better adjust the user interface to handle the features supported by these platforms. Both the desktop and mobile web site have been updated. This will be a welcome improvement to owners of these devices.
- MeshCentral Router Connectivity Improvements. MeshCentral Router is a popular tool used with MeshCentral for routing TCP and UDP traffic thru a MeshCentral server to any network where a MeshAgent is running. In the last month, MeshCentral Router got user interface improvements and more significantly, new connectivity settings so you can specify an HTTP proxy to use and, if needed, a TLS client certificate. The client certificate is interesting if MeshCentral is placed behind a reverse proxy and requires TLS client authentication to allow connections. This setup significantly reduces the attack surface when exposing MeshCentral to the Internet.
Many other features have been added and bug fixes included. As usual,
feedback is appreciated. If you see any problems or need support on
something, please create a new issue on GitHub or help other users. For more information, visit the portal at https://meshcentral.com.
Enjoy!
Ylian
MeshCentral, Blog, Twitter,
Reddit, GitHub, YouTube.