MeshCentral2 - Security, DB Record Encryption, Vault support
Because MeshCentral is a web site that has control over a lot of devices, security is super important. MeshCentral already implements two-factor authentication, FIDO2 hardware keys support and much more. In the last few months, we added even more security features to insure that compute assets are as protected as possible. Here are some of the security features that were added recently:
Of course, no software is fully secure. In case of any concerns or security issues, one should contact the developers. A new PGP key is now available for anyone that wants to send confidential files or messages. Security is an ongoing process and so, we look forward to more feedback from the community on how to improve MeshCentral even further.
Enjoy,
Ylian
Twitter: https://twitter.com/meshcentral
Reddit: https://www.reddit.com/r/MeshCentral/
GitHub: https://github.com/Ylianst/MeshCentral/issues
MeshCentral2: http://www.meshcommander.com/meshcentral2
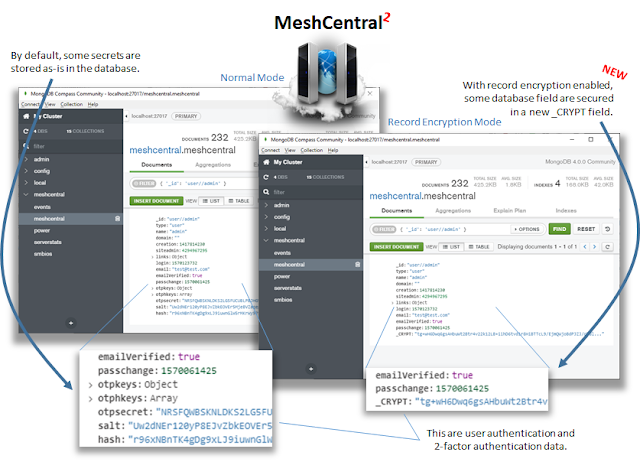
- Database Partial Record Encryption. When saving data in the database, some of the fields will need to be indexed for fast retrieval, but some of the data is sensitive such as account two-factor keys and Intel® AMT credentials. For these values, MeshCentral now offers an optional additional encryption layer using AES256-GCM. Fields that are marked as sensitive are encrypted and encoded in a special _CRYPT value in the database. When reading the record back, MeshCentral decodes and places the sensitive fields back transparently to the rest of the server code. This feature can be used on top of encryption features offered in the database itself.
- HashiCorp Vault support. Vault is an open source secret management software that is used to store configuration settings, keys and certificates. You can get more information about this software at vaultproject.io. MeshCentral now supports storing and retrieving configuration and certificate information from Vault. This has many benefits: It allows the MeshCentral server to keep no secrets at rest, improving security. It allows MeshCentral to be completely stateless when running in a Docker container. It also allows for centralized management of secrets. All you need to specify is how to connect to Vault and all configuration is retrieved including MongoDB settings, etc. This is done before connecting to the database, so the database connection string and credentials can also be stored in Vault.
- Cookie & Token IP address binding. MeshCentral session state that is sent to the browser is now bound to the external IP address of that browser. If malware obtains a user’s browser session data, it can’t use that data from a different IP address. The server will detect and reject use of session data from a different external IP address increasing the security of session information.
- MeshCentral Security Features Guide. In order to better inform MeshCentral administrators of the default and optional security features of the server, we have a new one page PDF guide highlighting the top 12 security features of MeshCentral. This makes it easy to see what features are available. For more details on any given features, take a look at the MeshCentral User’s Guide.
Enjoy,
Ylian
Twitter: https://twitter.com/meshcentral
Reddit: https://www.reddit.com/r/MeshCentral/
GitHub: https://github.com/Ylianst/MeshCentral/issues
MeshCentral2: http://www.meshcommander.com/meshcentral2
Check out the MeshCentral
Security Features Guide (PDF)