MeshCentral2 - Hardware Key Support, One-time Passwords, Running Stateless
MeshCentral is an open source web based remote computer management web site. Because administrators can use MeshCentral to manage hundreds to thousands of computers remotely, the server is a security target. It’s important to support the best industry practices to try to minimize security risk. This week, three new security features where added to MeshCentral.
Enjoy!
Ylian
MeshCentral2: http://www.meshcommander.com/meshcentral2
Twitter: https://twitter.com/meshcentral
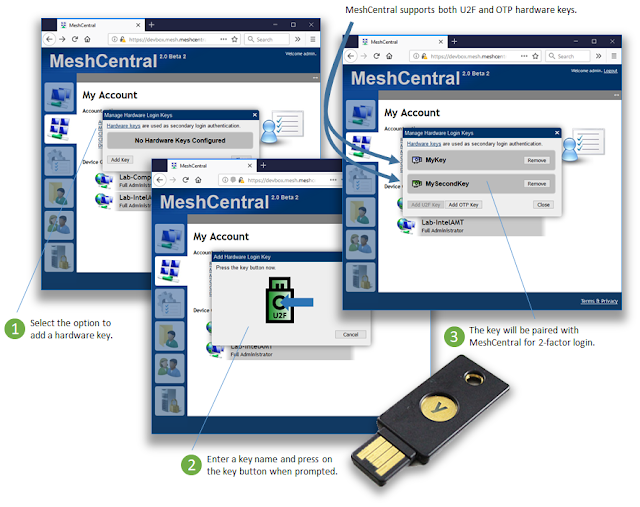
- Support for hardware authentication keys. A few weeks back, work got started on adding 2-factor authentication to MeshCentral. First, with support for Google Authenticator. This week, we improve on this with support for hardware keys. You can get a YubiKey starting at 15$ that acts as a hardware based second authentication factor. Users first have to register their key with the web site. Then when logging in and after entering the username and password, user’s will be prompted for a login token. At this point, press the button on the USB key and
your automatically logged in. It’s super simple and can be used alongside Google Authenticator. Two hardware keys modes are supported:- U2F mode. In mode requires browser support. Chrome supports it fully and FireFox can support it when the option is enabled. In this mode, the hardware key perform a signature of a challenge request. Details here.
- OTP mode. In this mode, the key acts as a USB keyboard and enters a long one-time string when activated by the user. This mode will work on any browser but MeshCentral needs setup and will query the YubiKey server for validation. Details here.
- Support for one-time written down keys. To complete the 2-factor authentication offerings of MeshCentral. If you don’t have your phone or hardware key, there is now an alternative that is often used as a backup. MeshCentral can generate a set of one-time-only numbers that can be used as a second authentication factor. Users generally print and keep these numbers in a safe place. When presented with the 2nd factor login screen, users can enter a one of the single use 8 digit token.
- Running the server stateless. MeshCentral got a new set of features to allow administrators to load the configuration files of the server into the database. When doing so, an encryption key is mandatory and AES256-CBC is used to encrypt the configuration files before adding them to the database. Once done, a MeshCentral server can launch and with only the connection string to the database and decryption key, the server can launch correctly. Why would this be interesting? With increased security regulations that requires “encryption at rest” the server can store everything in a security compliant database. Also, there is an expectation that Docker containers run stateless. This new mode makes the server run perfectly in this model and MeshCentral containers can be started and stopped without having to worry about container state.
Enjoy!
Ylian
MeshCentral2: http://www.meshcommander.com/meshcentral2
Twitter: https://twitter.com/meshcentral
MeshCentral now supports U2F and OTP Hardware Authentication Keys.
OTP works on all browsers, U2F on select browsers that support it.
OTP works on all browsers, U2F on select browsers that support it.
In addition to supporting time limited tokens with Google Authenticator and hardware keys,
MeshCentral now support written down, one-time login tokens.
MeshCentral now support written down, one-time login tokens.
MeshCentral can now run “stateless”. That is, all of the server
configuration is located in the database. This improves deployments of
MeshCentral in Docker containers and improves security.